Hello World,
You might get surprised by the title of this post. Usually, Group Policies are specific to Windows environment and are not really used with Ubuntu Desktop solution. However, since Ubuntu 22.04, Ubuntu Desktop operating system can take advantage of Active directory group policies. Canonical, the company behind Ubuntu is targeting more and more corporate environment and try to offers more and more paid services to enterprises. This is becoming more and more obvious. Look at the Ubuntu Pro subscription offering or Landscape Server and now the AD integration and GPOs.
This post will have a quick look at AD integration and Group policies capabilities made available in Ubuntu 24.04. So, Let’s move on !
Overview
Introducing ADsys client
Microsoft Active Directory Identity management solution is probably one of the most deployed solution in corporate environments. Because of this omnipresence, it was logical that Linux distributions would come up with a way to integrate with Active Directory. Nowadays, majority of Linux distributions support Active directory integration through the usage of SSSD package. Ubuntu supports this integration for some time now and offers also the possibility to join Active Directory during the Setup process. This feature is around since Ubuntu 22.10 (if I remember correctly).
By simplifying the process to join Active Directory, Canonical is positioning Ubuntu as a real desktop alternative and help to leverage Active Directory investments. This feature is providing really interoperability between Ubuntu Operating system and windows Operating system and the best part is that the process is really simple and appealing to companies. We have already published some posts about AD integration and Ubuntu
- Ubuntu – Join Ubuntu 20.10 Desktop in Active Directory Domain during Setup
- Ubuntu – Join Ubuntu 20.04 to Active Directory – How To
- xRDP – Remote Connection to Ubuntu Using Active Directory Authentication (HowTo)
The SSSD package allows you to join an Active Directory Domain and perform Kerberos authentication against it. Some basic GPO were also available to the Linux machine but the scope is quite limited. To overcome this limitation, Ubuntu 22.04 has introduced the ADsys component which allow an even stronger integration with Active Directory and enable deeper Group Policy integration for Ubuntu machines.
With the release of Ubuntu 24.04, Canonical has emphasized a little bit more this feature and provided some documentation and guidance on how to use this feature. ADsys is a software component that will provide everything needed to integrate your Ubuntu to Active Directory including administrative templates (admx and adml files). ADsys is not a SSSD replacement which is still needed to access Active Directory. ADSys is extending Ubuntu capabilities when joining Active Directory Domains. Using ADsys, you can use the following features
- Native Group Policy Object support for both machine and user policies
- Privilege management, allowing the possibility to grant or revoke superuser privileges for the default local user, and Active Directory users and groups
- Custom scripts execution, giving the possibility to schedule shell scripts to be executed at startup, shutdown, login and logout
ADsys & Ubuntu Pro dependencies
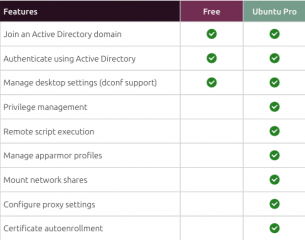
As mentioned in the beginning of this post, Canonical is clearly developing its commercial strategy to make money from the eco-system they have created. Canonical wants you to subscribe to their Ubuntu Pro Subscription program so you can benefit from all the features provided by the ADsys client and extended Active Directory integration capabilities. The following table summarize which features are free to use (no Ubuntu Pro needed) and the one needing Ubuntu Pro Subscription
Click on Picture for Better Resolution
So, you will have basically 2 flavors of AD integration capability. You will have the
- Basic AD integration feature (which is free)
- Advanced AD Integration feature (where Ubuntu Pro Subscription is needed)
Using the basic AD integration feature, you will be able to join Active Directory, Authenticate against it and control through GPO some desktop settings such as wallpaper or login screen. Any other features will require to use Ubuntu Pro. As a reminder, Ubuntu Pro is free for personal usage up to 5 computers. So, technically, you can still test scripting or privilege management features as well.
How To use ADSys and Ubuntu GPO Templates
In this section, we will try to join an Ubuntu machine in an Active Directory and see how Active Directory GPO could be applied to this Ubuntu machine. Since we have no attach the test machine to Ubuntu Pro subscription, we will be limited to implementing only Desktop and login screen GPO settings.
Join Ubuntu to your Active Directory Domain
Assumptions & Scenario
In this post, we will assume the following
- You are running Ubuntu 24.04 Desktop
- You have already an Active Directory up and running
- Active Directory is providing Time services
- You have internet access in order to download the additional packages that needs to be installed
If you have all these prerequisites met, we can move to the next section
Initial Ubuntu Desktop Configuration Settings
Before attempting to join Active Directory from your Ubuntu 24.04 Desktop, you will need to perform some pre-configuration activities. Indeed, in order to successfully join AD Domain, you will need to configure you machine with the following settings
- Fully Qualified domain Name (matching the AD Domain name)
- Configure proper DNS so name resolution for AD Domain would be possible
- Configure Time services (needed for Kerberos authentication and validation)
- Installing necessary packages on Ubuntu to enable Authentication to remote directory service.
We will not go into details here about how to join ubuntu into Active Directory. You can find detailed information in the following post
Step 1 – Installing SSSD software & Tools
So, first we will need to install sssd packages on the Ubuntu 24.04 desktop computer by issuing the following command in your Terminal console
sudo apt-get install sssd-ad sssd-tools realmd adcli adsys
Wait for installation to complete and move to the next steps
Step 2 – Configure Hostname settings
In this step, we will ensure that our Ubuntu machine is already configured with a proper name and that the fully qualified domain name is used. So, in our scenario, the FQDN will look like ubuntuwks01.c-nergy.lab. To set this FQDN, we will issue the following command in a Terminal console
FQDN="ubuntuwks01.c-nergy.lab" sudo hostnamectl set-hostname "$FQDN"
To check that the change is applied accordingly, you can issue the following command
hostname -f
This command should return the FQDN you have defined
Step 3 – Configuring valid DNS Servers on Ubuntu machine
If you are using a DHCP infrastructure, no need to perform any changes as long as the DHCP server provide the IP address of the Active Directory DNS server. If you are using a static ip address, you might need to change the DNS Server Address in your Ubuntu machine to point the AD DNS server.
Step 3 – Configure Time services on Ubuntu machine
By default, Ubuntu get its time from a public NTP server (usually ntp.ubuntu.com). To ensure that no time drift would occur, we will configure our Ubuntu machine to point to the Active Directory Time Source Server. In our scenario, we are using the Domain controller in AD as authoritative source for our Ubuntu machine.
To configure time service, edit the file
/etc/systemd/timesyncd.conf
Look for the NTP line. Delete the information and enter the FQDN of your Time source server
At this stage, we should be ready to move forward to the next step….
Connecting to Active Directory
Step 1 – Discovering Active Directory
At this stage, we should be ready to connect to your Active Directory. Indeed, we have installed the necessary packages to “talk” to Active Directory (i.e. SSSSD) and the name resolution process has been configured accordingly (ip address and dns server settings). Before we effectively join the domain, we will first check that our configuration is valid and that we will be able to join our Active directory domain.
Open a Terminal console and issue the following command
realm discover <%AD Domain Name%>
As shown in the screenshot below, if your configuration is correct, you should see information about the AD domain you are about to join. Notice the line Configure : no which basically tells you that you are not yet connected to the Active Directory
Step 2 – Join Active Directory
If you can discover Active Directory from your Ubuntu machine, you probably have performed all the needed configuration. You are ready to join the AD domain. So, Open a Terminal console and issue the following command
realm join <%AD Domain Name%> systemctl restart sssd
You can check that you have joined AD correctly by querying group membership of an AD User account. Usually, we use administrator user account. To do that, simply issue the following command in Terminal Console
id Administrator
You should see some groups information in the console as output.
Step 3 – Create AD Home Directory
You will need to issue the following command to ensure that active directory users login into the ubuntu machine would get their home profile directory created on the machine. Open your terminal console and issue the following command
pam-auth-update --enable mkhomedir
Uploading Ubuntu admx files in Active Directory
Step 1 – Obtain the admx files from your Ubuntu machine
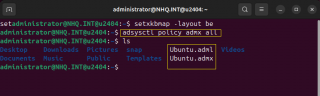
There are multiple ways to obtain these files. You can download them from github page or probably the easiest way would be to issue the following command
sudo adsysctl policy admx all
This command will generate 2 files
- Ubuntu.admx
- Ubuntu.adml
Click on Picture for Better Resolution
You will need to copy these files in one of your Domain controller in the following location
.admx C:\Windows\SYSVOL\domain\Policies\PolicyDefinitions\ .adml C:\Windows\SYSVOL\domain\Policies\PolicyDefinitions\en-US\
Step 2 – Review and Configure your Ubuntu GPO from your Active directory
Note: We assume that you have experience with GPO and you understand terms and technology.
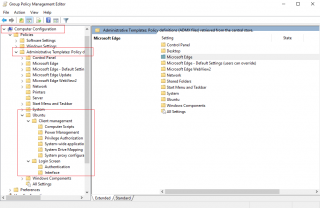
When the admx and adml files for Ubuntu settings have been copied on your domain controller on the correct folder location (see above), we can have a look at which settings can be configured. So, let’s g o on a windows machine where you have the Group Policy management console installed (gpmc) and open it. Create a new GPO targeting Ubuntu machines. When the GPO is created, you will be able to check which Ubuntu Settings can be configured through GPO.
As you can see on the screenshot below, Ubuntu admx templates offers settings for Computer settings and for Users settings as well. As you can see, you could configure startup/shutdown scripts, control user and access rights (Privilege identity management or simply customize the look’n feel of your Ubuntu machine). These settings can be the login screen or the wallpaper to be used.
Click on Picture for Better Resolution
Click on Picture for Better Resolution
Configuring GDM Login Screen using Group policies for Ubuntu
Since we have recently published some posts about how to customize login screen on Ubuntu machines (and since this machine is not attached to Ubuntu Pro Subscription), we will use try to configure a GPO that will be able to
- set a specific background image for the login screen
- Set a banner message on the login screen as well
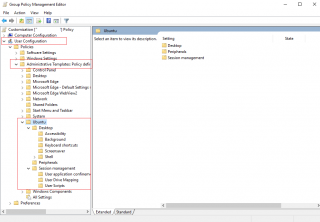
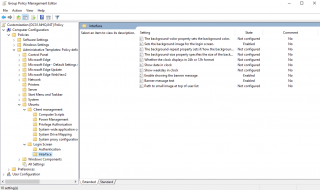
We assume that you have all your ubuntu machines located under a dedicated OU (called Ubuntu for example) and that a GPO called Login Customization has been created and linked to this OU. We will edit this GPO and set the following settings under the Computer Settings > Administrative Templates > Ubuntu > Login Screen > Interface
Click on Picture for Better Resolution
We have enabled the following settings
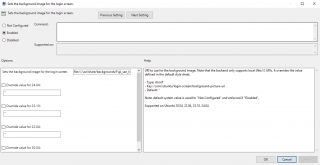
- Set background image for the login screen and the screenshot below shows the settings we have used
Click on Picture for Better Resolution
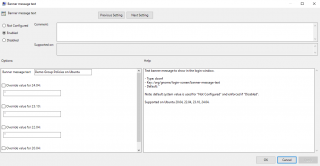
- Enable showing Banner message & Banner message text
Click on Picture for Better Resolution
You can decide to wait for the GPO to apply to your Ubuntu machine or you can use the equivalent of gpupdate /force on your Ubuntu Client which is the adsysctl command. So, execute the following command on your Terminal console and logoff from your session and check your login screen
adsysctl policy update -av #To check policies applied on the system you can run the following command adsysctl policy applied --details
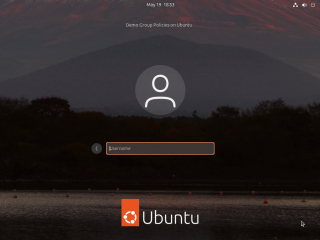
If the GPO applied correctly, you should see your newly configured login screen and the banner message configured as demonstrated below in the screenshot
Click on Picture for Better Resolution
Final Notes
This post is becoming a little bit too long. So time to close it here.
In this post, we have seen that Ubuntu can take advantage of Active directory and Group policies. We have quickly described how to join Active Directory and implement group policies against an Ubuntu Desktop computer. There are multiple settings that you can customize but compare to windows they are still limited. The existing GPO can control the Desktop settings, Privilege management and startup/shutdown scripting. The important thing to remember is that if you want to take full advantage of this GPO integration, you will need to have an Ubuntu Pro Subscription.
There are many other settings that can be implemented which can help in managing and securing Ubuntu Desktop when integrated with Active Directory. We have only scratched the surface here. We think that these features and the possibility to use Active Directory and the GPO is a great addition for corporate infrastructure. If time permit, we might publish another post about this topic….
Till next time
See ya
Additional readings & References:
- https://ubuntu.com/blog/new-active-directory-integration-features-in-ubuntu-22-04-faq
- https://ubuntu.com/blog/ubuntu-pro-enhanced-security-and-manageability-for-linux-desktop
- https://canonical-adsys.readthedocs-hosted.com/en/stable/

There is a syntax error in:
sudo adsysclt policy admx all
It’s adsysctl
@Thomas,
Thank you for the feedback and visiting our blog.. . good catch… The post is being updated and corrected
Thank you for letting us know… we will correct the typo and make sure the instructions are correct
Till next time
See ya
Greeting Griffon,
Your blog is more useful for me and i have done setup the Windows AD domain with 100+ Ubuntu clients.
Currently I plan to push a bash script to ubuntu client machine using the windows AD Domain GPO.
Computer Policies -> Ubuntu -> Client management -> Computer Scripts -> Startup scripts
But I can’t succeeded.
Kindly please help me.
I need your help here.
If the startup script runs on ubuntu machine it will covered all ubuntu machine control.
Thanks and Regards
George
Greeting Griffon,
Also please send here How to block in ubuntu client machine USB pen drive for particular Windows AD GPO login users.
Thanks and Regards
George
@George,
Thank you for visiting the blog and providing feedback. Sorry for the delay in answering…
so to have scripts running on UBuntu from AD GPO, you need to ensure that
1. The ubuntu machine is using UBuntu Pro subscription => this is a requirement to have the scripts feature working when using Ubuntu GPO
2. Scripts must be available Active Directory sysvol share. More specifically, you need to copy scripts in \\domain.name\sysvol\domain.name\scripts.
3. each time you change the script, you need to increment value in the Gpt.ini file of the gpo. There is a way to automate this process…but didn’t got time to write about it
if you meet these conditions, you should be able to get your scripts running on Ubuntu.
Hope this help
Till next time
See ya
@George;
Ok we will need to look into this one.. but we think that udev could be used to block usb on a per user base. you could use polkit rules to block usb… maybe you can remove the user from plugdev group as well so he cannot mount devices…
Hope this help
Till next time
See ya
blocking the installation of app possible using GPO .Can you insturuct me to do
@John,
Thank you for visiting our blog and sharing your experience. So; not sure we can block ubuntu app install through the GPO. GPO for Ubuntu is providing some support but the scope is rather limited. To perform the install, you should be prompted by sudo. Is this not good enough for you ? There might be other ways to block app install on ubuntu via some scripting but never tested or investigated this…. Maybe some of our readers can help here ?
Till next time
See ya