Hello World,
I know ! It’s a long time I haven”t post some stuff… but he, I’m busy as well..I have to work on some projects abroad. Today’s post will focus again on PROXMOX VE (PVE) software and we will quickly check the networking model provided by the software.
Ready ? So, let”s start
PROXMOX VE and network model.
PROXMOX VE can be integrated in small network infrastructure or can be member of a more complex LAN Topology. PROXMOX VE can be configured with Bonding devices, bridges devices and provide VLAN support. All these options will allow you to create complex topology.
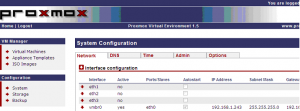
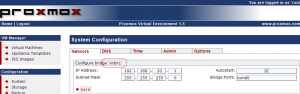
PROXMOX VE uses bridged networking model. After you’ve performed the initial installation, you will get something similar to the following screenshot
Click to enlarge
In the Configuration Section, on the System Configuration Node, you will see a list of the physical network devices and also a object called vmbr0. This object is basically your bridge. A bridge act like a physical switch. If you inspect the properties of the vmbr0 object, you will see that the bridge is associated with a physical interface (eth0) and an IP address. This IP address and this bridge give you access to the PVE host on the network. If you do not like the initial configuration, you can decide to modify the settings and create bonding devices and bridge devices.
What’s a bonding device ?
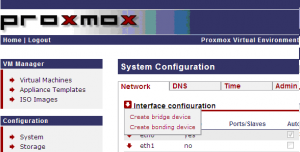
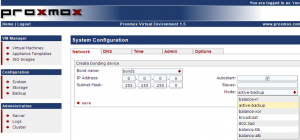
In a few words, bonding device offer you the possibility to group together multiple physical network card and make them act as one. This is also called teaming. In the Configuration section -> System Configuration page, click on the arrow next to the interface configuration, select “Create Bonding device”. In the bonding page, you can specify the IP address and subnet mask, you can specify the physical network cards that will be bonded and the mode.
Click to enlarge
The mode dropdown box will provide you multiple choices
- balance-rr : this mode transmit packets in sequential order from the first available slave through the last. This mode provides load balancing and fault tolerance
- active-backup : in this configuration, only one Network card is active. if the active card fails, the passive card will take over
- balance-xor : This mode transmit packets based on hash policy. this mode provides load balancing and fault tolerance
- broadcast : This mode transmits packets on all slave interfaces. This mode provides fault tolerance
- 802.3ad : advanced – dynamic link aggregation. To use this option, you will need to configure you switch to support/configure 802.3 features
- balance-tlp : advanced – adaptive transmit load balancing. Outgoing traffic passing through all slaves but only the active card receive traffic. It the active card fail, the MAC address is taken over by a remaining passive network interface – No switch configuration needed to use this mode
- balance-alp : advanced – This is adaptive load balancing support and no switch configuration needed
Note :
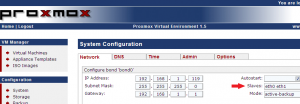
I would recommend (if your hardware have enough Network Interfaces) to configure your PVE Host to use bonding devices (for production systems). This will provide redundancy to your system. This is not mandatory. You could run your PVE Host with only one network card. On my system with 3 network interfaces, I’ve bonded the first two together. Check out the notation for the slaves. Simply add the physical interfaces separated by a space.
Click to Enlarge
When this is done, you the Configuration Section ->System Configuration Page -> network tab, you will see in your list the interface “bond0” (your bonding device) and note that the physical interfaces you’ve used as slave will not be listed anymore. You cannot use them anymore for creating bridge devices
What’s a bridge device ?
As explained a little bit earlier, a bridge will act as a physical switch. You could connect cable into it and provide network connectivity using the brige devices. If you click on the create bridge device…
you will end up in a web page, where you will be asked to provide IP address and which network card you want to associate to the bridge. In the screenshot below, you can see that i’ve specified the bond0 device instead of a standalone physical network (ex:eth3).
Click to Enlarge
Note :
If you want to, you can also create a bridge device and not associate it to any network interfaces. If you connect virtual machines to a bridge with no network cards associated, you are basically creating a internal-network only configuration. These virtual machines will be isolated from the rest of the network given that they have no network connectivity (through the physical network card)
Advanced Configurations
So far, we haven’t done any exotic configuration. The configuration of the network for our PVE host has been done through the Web Interface. If you need to have more advanced configuration (such as routed configuration or masquerading), you might need to update the file /etc/network/interfaces.
<<—— Example Content of /etc/network/interfaces —->>
<<- – Default brigded configuration using bond0 as bridge ports —>>
auto lo
iface lo inet loopback
auto vmbr0
iface vmbr0 inet static
address 192.168.1.12
netmask 255.255.255.0
gateway 192.168.1.1
bridge_ports bond0
bridge_stp off
bridge_fd 0
<——– END of File ———————>
If you need to have your virtual machine on a separate subnet, you can create a network configuration that will allow you to use NAT technology.
Imagine the following scenario :
you have your PROXMOX VE located on the subnet 10.10.10.0/24 and you need to have your virtual machines located on the subunet 10.10.20.0/24 but you want to have your virtual machines to be able to access the subnet 10.10.10.0/24 (and vice versa machines located on 10.10.10.0/24 should have access to the virtual machines).
Using PROXMOX VE technology and networking model, you can achieve this result by using a technic called masquerading in linux world. Masquerading is really similar to NAT technology. You will create your bond0 and configure your bridge (vmbr0) as described above. But in order to interconnect subnet 1 (10.10.10.10/24) with subnet 2 (10.10.20.0/24), you will need to update the /etc/network/interfaces and add the following lines (in bold)
(….)
auto vmbr0
iface vmbr1 inet static
address 10.10.20.1
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.20.0/24' -o bond0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.20.0/24' -o bond0 -j MASQUERADE
This command will instruct the PVE host to pass traffic between virtual machines and PVE Hosts and other machines located on the different Subnets !
As you can see PROXMOX VE offers some capabilites and can be integrated in a complex LAN topology (including VLAN). WIth this post, we have just presented some basic configurations. In future posts, we will detail a full setup of a PROXMOXVE covering different scenarios.
Till next time
see ya
Hi Griffon
Very nice info! Are you going to do a post on vlan setup in Proxmox anytime soon?
Regards
Yes,
As soon as i have some time, I would love to post back some information about PROXMOX VE and the VLAN Settings. Foreseen Date…..Begin of January 2011
Thank you for your interest
Most excellent! Thank you Sir Griffon.
Excellent post! Your time dedicated to the novice people like me is very appreciated. Than you very much
Thank you for your comments…
As soon as I have more time, I’ll be posting more information about ProxMox Ve because this is a cool product
See ya
hi, griffon, thanks for your articles. very useful!
Here I have another question. If I am right, the concept “load balance” you refer in this post are all about network traffic load balance. So I am wondering have your ever researched in other kinds of load balance in promox? Thanks you.
Hello Jeff,
In this post, I was indeed referring to balance the network traffic.
I have not checked or tested any other load balancing stuff. I’ve setup a Proxmox VE Cluster providing your high availability and where you can maybe manually load balance the charge between your hosts.
If you want to load balance virtual machines (ex : you have 2 Web servers and you want to load balance traffic between them), I would use a software load balancer. Netscaler provides a free load balancer virtual appliance (with restricted functionalities). Using Netscaler, you can try to load balance between servers (virtual machines)
So far, I do not think that proxmox ve offer a way to load balance resource (like vmware) between proxmox ve hosts
I hope this answer your question
Best Regards
Afternoon Griffon
I don’t know if i have missed your post, did you perhaps post an article on “PROXMOX VE VLAN settings”?
Regards,
Belthazar
Hi Belthazar,
No, you haven’t missed it… I didn’t write it yet… I have made some tests already… but got no chances to publish it yet… I hope to publish something within the next 2/3 months….I’m travelling a lot for the moment (for work) so not always easy…
Thanks for reading my blog…I’ll really try to write over PROXMOX VE and VLAN SETTINGS…
Do you have a particular situation or is it to have a more general overview of the VLAN options in Proxmox VE,….
Let me know if you have a particular situation/scenario. I might then be able to responde more quickly to your request
See ya
Morning Griffon
What is the best way to configure vlans on proxmox (via cli or webgui ) and what should one keep in mind when deploying vlans using proxmox?
In short: I have 2 NICs, I would like to keep management to eth0 and publish multiple vlans and hosts on eth1. Somewhere I’m missing the boat.
Regards,
Hello Belthazar
To quickly answer your questions, I would recommend to use the Web Interface to create your VLAN. This feature is implemented within ProxMox VE. for advanced scenario, you will need to indeed go into the config file and modify it as required.
For the other question, I have posted a “quick and dirty” basic vlan configuration scenario here
Have a look . I hope that this would help you
see ya
Afternoon Griffon
Thank you VERY-VERY much, it is a COOL how to! Much appreciated.
Regards,
Hello Belthazar,
No Problem, hope that this post has answer your questions
Stay tuned for more info…about ProxMox VE
Yes, it did and it also made me realize how easy it actually is. Oh, these moments of being blonde!
I test mode 0,4,6 on 4 network cards,
No one can use both input and output to 4G or nearly.
why and how ?
euh I do not get the question
what’s mode 0,4.6
I know this is a bit outdated, However this still works with Proxmox VE 5.3, I do have a question though. I only have 2 NICs if I bound them can I still create a bridge for the VMs to communicate on? Also if I have n already established Cluster will this mess up my cluster? Should I remove each node, make the network config changes then add it back to the cluster?
Thank You,
Michael
@Michael;
I do not know all your configuration…But speaking generally, you can use bonding when PVE is clustered… This actually improve speed and resilience…. I would probably indeed remove nodes from cluster config and perform the change and see if this is accepted. If needed, you can also create additional virtual Nic for PVE and create your necessary bridging….
Hope this help
Till next time