Hello World,
As you have noticed, we have been quiet the last few weeks. The reason is quite simple. Work and Projects ! We had too many things to do and really few spare time for blogging activities. As holidays season is also there, do not expect to see too many posts in the coming weeks.
However, be assure that we are preparing some news posts for the coming weeks where we will be speaking about RDS 2012 R2 infrastructure and the small issues/tips/tricks that we have been discovering along with RDS implementation projects. RDS is becoming important because more and more people want to use it. RDS is a really good solution to centralize your infrastructure and to provide a new software delivery mechanism that can be cost effective and easy to manage.
But let back to the topic of the day… Interactive Login and remoteapp…
The Situation
We recently encountered an interesting situation where our customer was trying to block access to the Remote Desktop host session server for certain users. To be more precise, the customer wanted to block access to either full remote desktop or remoteapp access to a certain group of users….We have been asked to come up with some options as the customer didn’t had much experience with RDS solution. As you can imagine, there are multiple ways to implement such configuration.
Option 1 – Hide Collections on RD Web Server
The RDS infrastructure was accessed via the RD Web Server. So, initially, the customer tried to configure the RDS in order to hide sessions collections to specific users. This approach does not really prevent users to access the Remote Host Session Servers. You simply trying to hide your infrastructure. However, if a user is smart enough and knows the name of the Remote Host Session Server, this user can remote desktop into it and consume services from that server.
This option is not really preventing the user to access your infrastructure. You simply try to hide the RDS infrastructure to the users.
Option 2 – Deny Logon through RDS GPO
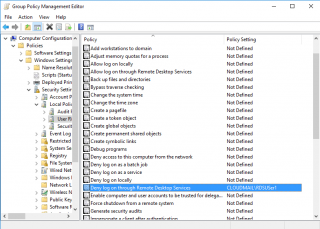
A possible better option would be to implement a GPO that will restrict the logon to the RDS Server. Indeed, user rights can be configured through GPO. There is a user assignment right called Deny logon through Remote Desktop Services.
Click on Picture for Better Resolution
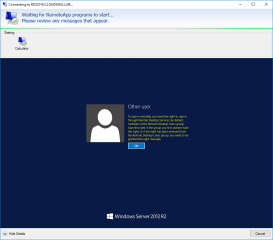
This option is preventing a user to perform a remote desktop connection into the server where this option is set. If a user tries to access the Remote Host session where this setting is implemented, the following error message would be displayed
Click on Picture for Better Resolution
This approach is valid and could be used to prevent access to remote Host session servers. However, as you can imagine, you will need to perform a little bit of preparation work before you solution is working properly. You need the appropriate groups, you need to create and apply the GPO, you need to test your gpo…..
The only drawback (I could imagine) with this approach is, you need to be familiar with GPO and you need to have the right to manage them. In big organizations, GPOS are managed by another division.
But again, this is totally valid and workable solution in Enterprise.
Option 3 – Active Directory Attributes
This option might be easier to implement and you simply need to have access to the Active Directory Management console to implement this. No need for GPOs and groups to be created. Actually, we came up with this solution as the customer was specifically requesting for a simple way to implement the settings (and knowing that gpo was managed by other teams)
So, how can you prevent users to interactively login into a remote Host Session using Active directory Attributes ? Follow these steps
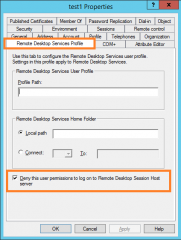
Locate the user to be blocked from login into the RDS in your Active Directory. Right-click > Properties. In the properties dialog box, go to Remote Desktop Services tab
Click on Picture for Better Resolution
At the bottom, you can see the option, Deny this user permissions to log on to Remote host Session Server. If you tick the checkbox, the user will not be able to access the Remote Host Session servers
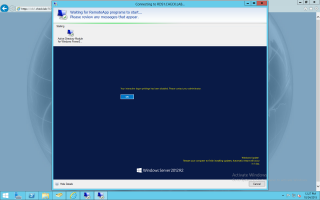
If the user tries to open a remoteapp published through the RDWeb Access, it will receive this error message. The same error message will appear if the user tries to perform a direct remote desktop connection to a RD Host Session server
Click on Picture for Better Resolution
This option only applies to RDS servers. If the user needs to access other servers using Remote Desktop, the user will be able to access them with no problem and this settings will not apply to him.
This is a cool and easy way to control who’s using your infrastructure
Using this third option, you would need to perform changes user per users. This method is kind of granular way to control your RDS infrastructure. If you need to perform changes in Bulk, you can always use Powershell to perform such actions
Final Notes
Voila ! This is it for this post. We have quickly explained how you could control which user can access your RDS infrastructure through two different methods. Based on your requirements and expectations, you might want to choose the best option for your organization. GPO that block logon through Remote desktop is a good option in well structured and organize enterprises.
The Active directory attributes look appealing for smaller organizations or provide a good way to delegate activities to a smaller team that already managing users accounts. Using this approach, they can also control who access the Remote Desktop Services Infrastructure
Hope you enjoyed this post
Till next time
See ya