Hello World,
It has been some times since my last post. As you can image, I’m quite busy with official business. But Today, I have some time an I want to quickly share a small tip that helped me recently in one of these projects.
The tip of the day – How to run “a program” under the system account”
The Scenario
Why would you run an application under the “System Account” ? This is not something you would do on a daily basis. However, in some situations, you might need to debug or troubleshoot complex situation where your local admin account is not enough.
During this project, the customer has made a lot of customization on their Windows systems and they have configured them with security in mind. Hardening of the workstations was a priority for this customer. The customer has removed a lot of security permissions at multiple levels (registry,file system, Windows system rights….). Everything was fine until this customer needed to deploy a standard commercial application. The application was writing a lot of information in the registry. Because of the hardening of the system, there was no way to install this application. The application just through an error and the setup didn’t complete at all !
Finding a “Solution”
One option would have been to use some tools (like process monitor) to investigate and try to identify where the application was trying to write information to but we were short on time.We had to go through another path. We needed a quick fix for this customer.I do not know how it came into my mind but when searching for a solution I asked myself a really “simple” question : who would have more rights than the administrator account in this situation ? Eureka, system account might have more rights than the local administrator rights in my current scenario. the customer had change a lot of security rights related to “regular” accounts not the system accounts.
At this point, we had a possible workaround for this customer. We needed to test and validate this workaround. We needed to see how we could run the setup process using the system account
Testing and Validating the solution
Option 1 : PSEXEC utilty
The best way to run an application under system account and interactively is to use the “psexec” utility (can be founded here). This utility will work smoothless under any operating system (Windows XP, Vista, Windows 7)
Simply download the utility, accept the license agreement and from a command line, type the following command :
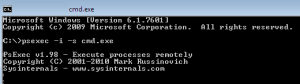
psexec -s -i “cmd.exe”
- -s switch indicates that you want to run with the system account
- -i switch indicates that you want to run in interactive mode
- cmd.exe is the program i want to run under system account
Fig 1 shows you the command that we have to execute if we want to run a “program” under system account
click to enlarge picture
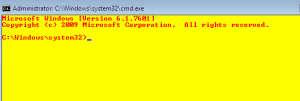
Fig 2 shows you the “program” (in my case cmd.exe) running under the system account. Note the background color change. It’s a visual tip that will remind you that you are running under system account. Another simple test to check if you are effectively running under the system account is to type in the yellow command prompt box the command whoami and it should return something similar to nt authority\system
click to enlarge picture
Option 2 : SC Utility
source : http://myitforum.com/cs2/blogs/jnelson/archive/2008/02/15/112673.aspx
Another option if you do not have the PsExec utility is to use the SC.exe utility. This command is available by default on Windows 7 and Windows Vista (I’m not sure for Windows XP). The sc.exe utility was part of the resource kit in Windows 2000. If not present on your system, you can always download it. To run as a service account, you simply need to create a batch file similar to the following
Credits : http://myitforum.com/cs2/blogs/jnelson/archive/2008/02/15/112673.aspx
@echo off
sc create CmdAsSystem type= own type= interact binPath= “cmd /c start cmd /k (cd c:\ ^& color ec ^& title ***** SYSTEM *****)”
net start CmdAsSystem
sc delete CmdAsSystem
On Windows XP systems, this will simply open a “yellow” command prompt indicating that the system account is used here. On Vista and Windows 7, you will not get access to the yellow command prompt automatically. Because these 2 systems are more secure, you will need to “authorize” the access to this new command prompt.
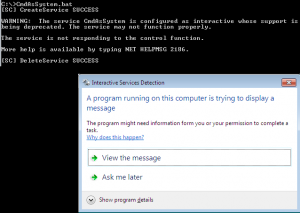
The following screen shot shows you that when the batch file runs, you might get the following popup (if not popping up, look at a blinking tab located in the taskbar). To access the “yellow” command prompt, you will need to click on view the message option
Click to enlarge picture
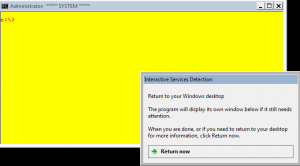
After clicking on the “View the message”, you will get something similar to the following screen shot. As you can see, the yellow command prompt is there waiting for you. Now, you can perform your operations. When done, you simply click on the Interaction Services Detection dialog box on the Return now and you are done
Click to enlarge picture
Final Words
And voila ! As you can see, the easiest way to perform such operations is to use the psexec utility even if other ways exists. The psexec utilty seems to be compatible with the new OS version of Microsoft.
At the end, using this approach, we were able to perform the requested installation for the customer. We even developed a small script that would run from a central location and launch the process on multiple computers on the network.
Enjoy
Till next Time
See ya
I like the screaming yellow cmd window in the SC method
So why not do this for the psexec method as well?
Here’s the line:
psexec -s -i cmd.exe /k (cd c:\ ^& color ec ^& title ***** SYSTEM *****)
And here’s the slightly easier to read yellow background, black text:
psexec -s -i cmd.exe /k (cd c:\ ^& color e0 ^& title ***** SYSTEM *****)
Hello Bortech,
Thank you for the comment and the tip…
We are exploring 2 options. One is psexec and the other is SC.Exe. We wanted to focus a little bit more on SC and not psexec tools…
Till next time
See ya