Hello World,
Today, we will publish a short post about xRDP and a new security Fix that has been released by the Team. The fix is out since September 27, 2023 after a security issue has been discovered and documented. This release does not bring any new features and aim only to fix the discovered bug.
So let’s see what the issue…
Overview
This is a security fix release for CVE-2023-42822. This update is recommended for all xrdp users. We have copied the information provided by the CVE here below
xrdp is an open source remote desktop protocol server. Access to the font glyphs in xrdp_painter.c is not bounds-checked.Since some of this data is controllable by the user, this can result in an out-of-bounds read within the xrdp executable. The vulnerability allows an out-of-bounds read within a potentially privileged process. On non-Debian platforms, xrdp tends to run as root. Potentially an out-of-bounds write can follow the out-of-bounds read. There is no denial-of-service impact, providing xrdp is running in forking mode. This issue has been addressed in release 0.9.23.1. Users are advised to upgrade. There are no known workarounds for this vulnerability.
This bug has been categorized with Severity Medium by different organizations and the recommendation would be to upgrade to the latest version…
So, what do we need to do ?
Good Question.
So, if you are using a well established distribution like Ubuntu or Debian, and if you have performed the installation from the distribution repository, you might not be running the latest version of the xRDP package. Since this security issue affect all versions prior 0.9.23.1, we would expect that the maintainer of your distribution will update either their package and package version or update the latest package version provided by the xRDP Team. However, this is not automatic.
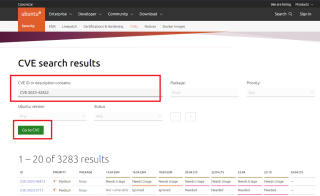
We can check the status of this security vulnerability from the Ubuntu CVE database by browsing to this url https://ubuntu.com/security/cves?package=linux. In this page, put the CVE number you look for (in our case, for this specific security issue), we would look for the CVE ID CVE-2023-42822
Click on Picture for better Resolution
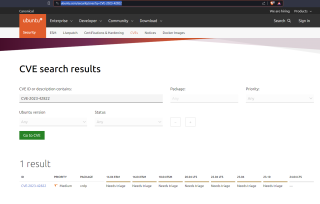
By clicking search, you will see the status of the security vulnerability. On this page, you can see that the status is set to triage and that no fix or patch has been yet released
Click on Picture for better Resolution
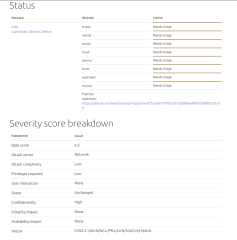
If you click on the link, you can have even more information about the bug, the score, vector attack….
Click on Picture for better Resolution
So, till now you can see that there is not yet a fix and at this stage, the status is set to triage. You will need to rely on the distribution maintainer that will decide to update or not the package. You can also decide to compile the latest xRDP package from sources and install the latest version including the security fix on your Ubuntu machine…. We have provided an easy to use xrdp-installer script that simplifies the compilation from sources for xRDP package…
If you have performed the installation from sources, you will have to update yourself the package. You should remove the version installed on your system and recompile from source. So, if you want to use the latest version of xRDP, you will need to compile the software from sources. You can also use our famous xrdp-installer script that simplifies and automate the installation (on Debian based systems). (see https://www.c-nergy.be/products.html). Please note that the latest version of the script has not been tested against xrdp pacakge 0.9.23 yet. So, use the script in a test environment first and validate your xrdp installation.
Final Notes
This is it for this post !
As promised, this is really a short post but rather important. Indeed, the xrdp team has made this latest xrdp release available (0.9.23.1) in order to fix some security issues that you should be aware of. If you are running a previous version of the package, it would be wise and recommended to install the latest version of the package.
Please note that the xRDP package shipping with your Ubuntu Operating system might not be the latest release version. You will need to check if some updates would be made available by the OS provider. If no updates are provided, you might want to build from sources and deploy the latest version of the xRDP Package… At time of writing, Ubuntu is not providing any updates of the xrdp package as shown in their cve web page (see : https://ubuntu.com/security/CVE-2023-42822).
The xrdp-installer script version 1.4.8 could be used to remove and install the latest version of xrdp package. The script 1.4.8 has not been tested yet against xrdp 0.9.23.1 package but it should be working as expected.
Stay tuned…
Till Next time