Hello World,
By default, when you install xrdp package on Ubuntu, any user defined on the machine can perform a remote connection to the Ubuntu machine. However, in some environment, the sysadmin might need to restrict or control who can effectively use the Remote connection capability. This post will explain how to perform just that.
So, let’s start our journey
Overview
As mentioned earlier, once you have installed the xRDP package, any user defined on the machine can basically perform a remote session against this machine. In certain situation, you might want to limit who can perform remote session against your Ubuntu machine. xRDP software has foreseen this scenario and offers a rather easy way to configure it. xRDP software provides some control and configuration tweak through the sesman.ini configuration file… We will quickly explain how you can achieve this in the following section…
Understanding xRDP Settings
The sesman.ini options
xRDP software solution uses a series of configuration files (sesman.ini,xrdp.ini) that can be used to control and/or customize your xRDP implementation. If you want to control who can access a remote session and prevent some other users, you will need to edit and modify the following file
/etc/xrdp/sesman.ini
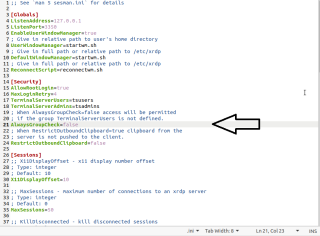
The content of the file looks like this
Click on Picture for better Resolution
If you look at the section [Security], you will see that you have some options to grant/prevent access to remote session capabilities. The section below shows you the default information about accessing the remote session and how you can control it
[Security] AllowRootLogin=true MaxLoginRetry=4 TerminalServerUsers=tsusers TerminalServerAdmins=tsadmins ; When AlwaysGroupCheck=false access will be permitted ; if the group TerminalServerUsers is not defined. AlwaysGroupCheck=false
This is the default configuration. This configuration simply tells xRDP that anyone can access the system remotely. Indeed, when installing xrdp, no specific group is created on your system and since the option AlwaysGroupCheck is set to false, this simply means that since no specific groups has been created to grant remote session rights, any users can perform a remote connection.
So, if you want to change the way users access your remote session, you will need to modify this file accordingly (and some other minor modifications on your system)…
Let’s do this !!
Configuring access to your xRDP Server
So, now, if you want to control who can access your xRDP server, you will need to
- Create a group
- Populate the group with users that needs Remote session capability
- Modify the /etc/xrdp/sesman.ini file
- Restart the machine (or the xrdp daemon) to commit the changes
Step 1 – Create a local group
The name of the group can be anything. If the sesman.ini file, there is a group name already defined which is tsusers. So, let’s assume we want to create this group in our xRDP server, we will issue the following command
sudo groupadd tsusers
Step 2 – Populate the Terminaluser local group
Since the group is created, we will need add members into this group. Member of this group will be allowed to perform remote session against our Ubuntu machine. If you are not part of this group, you will not be able to login. To populate the group, issue the following command (change the value as required)
usermod -a -G tsusers <%allowedrdpuser%>
Step 3 – Modify the sesman.ini file
It’s time to change your sesman.ini file accordingly. In a terminal console, issue the following command
sudo nano /etc/xrdp/sesman.ini
Locate the security section within the file and update accordingly the values for TerminalServerUsers and AlwasyGroupCheck. Based on our example, the file should look like this
[Security] AllowRootLogin=true MaxLoginRetry=4 TerminalServerUsers=tsusers TerminalServerAdmins=tsadmins ; When AlwaysGroupCheck=false access will be permitted ; if the group TerminalServerUsers is not defined. AlwaysGroupCheck=true
Notes
- It seems that as soon as you have create the group on your system, xrdp ignores the value of AlwaysGroupCheck. We will perform some more testing to confirm this behavior
- There is an option call TerminalServerAdmins available in the sesman.ini file. Please be aware that this option is not working and has not been implemented yet in the xRDP software solution !!
Step 4 – Restart the machine or the xrdp daemon
To commit the changes, you can decide to restart the machine or simply restart the xrdp daemon(s)
Test your configuration
To test our configuration, we have created 2 users
- allowrdp
- denyrdp
Click on Picture for better Resolution
The allowrdp user is part of the tsusers. When performing the remote connection against our ubuntu machine, we have a successful connection and the user can perform his work through the remote session
Click on Picture for better Resolution
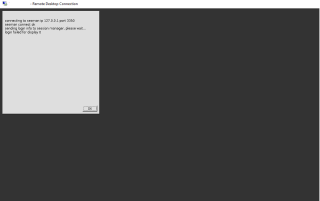
The denyrdp user does not belong to the tsusers group. When this user tries to perform a connection, connection will not go through and a dialog box might show up
Click on Picture for better Resolution
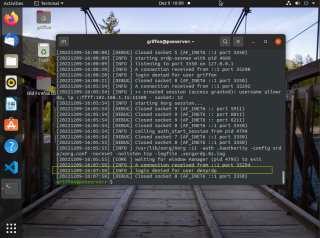
You can confirm that the denyrdp user has been denied access to the remote session by checking the /var/log/xrdp-sesman.log. You can see in the logs (screenshot below) who was granted access and who was denied access
Click on Picture for better Resolution
Final Notes
This is it for this post ! Now, you know how to configure your system to control who can perform a remote session or not. As you have seen, there are more options in the sesman.ini file. We have not covered all of them. Please do note that some options are present but they have not been implemented yet. So, it’s important that you check the Help file (man) for these settings in order to use them properly (you can check this link)
Hope you enjoyed this post
Till next time
See ya


Hello,
I appreciate the knowledge you share in your blog.
In our system there are many users who log in through the local network and have an “easy” password.
We’d like to set up a user that can access from an external network with a more serious password.
Is there any way we can allow a group of users to only access through the local network and let another group of users access local and external?
I thought maybe I could add a session type in xrdp.ini with a different port# and have only the superuser able to log in to that session and port forward that port# to the rdp server.
Any thoughts?
Thanks!
@Willy,
thank you for visiting our blog and sharing your feedback. Not sure about your setup. By default, All users can access the xRDP server as long as the server is accessible internally or externally. You can use groups to authorize or deny access to the RDP. Not sure your suggestion would work either….since we do not really know how you are planning to expose your xRDP externally. What do you call external ? is it from internet ? are you planning to use some reverse proxy ?
We would need to dig a little bit for this. However, our first recommendation would be to ensure that strong passwords are used when speaking about accessing Remote resources.
Till next time
See ya
I would never, ever, open up rdp to the internet. Use a vpn to connect to network and then start rdp session.