Hello World,
In this post, we are still looking into the Keeweb Software hosted on-premises on an IIS Microsoft web server. In our previous posts, we have looked into how to install and configure Keeweb software solution on premises and hosted on IIS Microsoft Web Server. We have been able to grant users access the Keeweb solution through a simple web browser and access the information stored in the “Keepass” database. You can find information about the setup in the following posts
- HowTo – Host your own Keepass on Windows IIS using Keeweb software – Part I
- HowTo – Host your own Keepass on Windows IIS using Keeweb software – Part II
However, we have noticed that with the proposed configuration so far, users can indeed have a read access to the information but the solution will not allow “authorized users” to update and modify entries in the Keepass database. In this part, we will try to tweak our configuration in order to allow users to update, change and save changes in the database
Let’s go !
Overview
Keeweb software is a modern password software solution that can be a perfect and easy to use solution for personal user. However, the software could also be used in a corporate environment as it seems possible to host the Keeweb software on a web server. A lot of our customers are running IT Infrastructure using Microsoft Software solution. This is why we are demonstrating how to host the Keeweb software solution on IIS Microsoft Web Server.
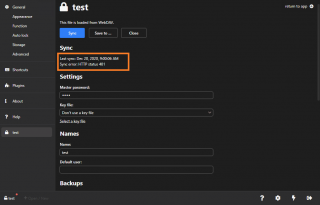
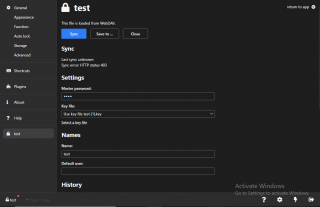
With our current setup, read only access is granted to multiple users through a web interface. The advantage of such configuration is that the password management solution is centrally available and managed. A customer came back to us mentioning that the current configuration didn’t allow to save changes in the database when accessing the software on the IIS Web server. After updating an entry, the user tried to saved the configuration and an HTTP 401 error was shown
Click on Picture for better Resolution
The other strange thing was that after logging off and on from the application, the user could see that modification was available in the interface. However, if another user open the application, the modification is not shown.
Click on Picture for better Resolution
This is kind of expected as the application is using web local storage to save changes. The local storage is based on per-user principle. This is why one user can see the change while another one cannot
Workaround – Use the Keeweb “Fat” Client
While we were working on finding a fix for the read/write issue, we offered a temporary workaround which would consist of update and maintain the Keepass database up to date. This can be cumbersome but can also offer some advantages as only a limited number of user can update the database. Obviously, this was not a sustainable solution and we needed to come up with a solution where read and write operations could be performed on the Keepass database…..
Configure IIS for Read and Write Access
It took us some time before we came up with a configuration that would allow users to create databases and to ensure that changes could be saved on the database file hosted on the WebDav server. The solution is based on two settings
- IIS Authentication option
- NTFS permissions on the Folder and kdbx file
Configuring IIS authentication
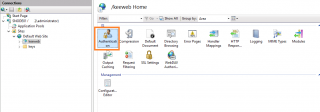
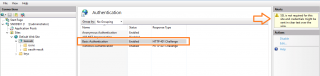
Going back to the IIS MMC console, we have to enable basic authentication method at the virtual directory level. To do that, you expand, Web Site > Keebweb directory. In the right pane, select the Authentication option in the mid pane
Click on Picture for better Resolution
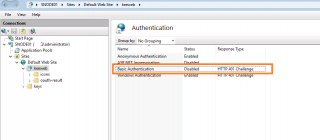
In the authentication method, you can see that the Basic authentication option is disabled
Click on Picture for better Resolution
Enable the basic Authentication option, Press Enable
Click on Picture for better Resolution
You can see the warning message about the SSL setting and clear text password that could transit through the network
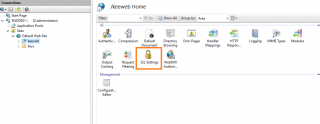
To ensure that SSL will be used, you can configure the IIS web server to force SSL usage. You can do this at the site level or at the Keeweb directory level. Let’s do this at the Keeweb Virtual Directory level. Expand and navigate to the Keeweb Virtual directory, in the right pane, click on SSL settings.
Click on Picture for better Resolution
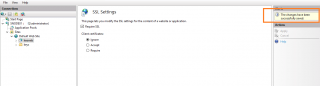
In the options, ensure that the require SSL checkbox is selected and press Apply
Click on Picture for better Resolution
To avoid that password are send in clear text, it’s really important that SSL connections are used when accessing the application through the web browser.
Important Notes !!!
Since we are using SSL configuration, we need to ensure that valid certificates will be used and trusted by clients through the network. You can use either a commercial and trusted certificates or your can use a self signed certificates. If you are using Self signed certificates, you can use GPO (group policies Objects) to ensure that this certificate would be trusted by workstations through your network
Configuring NTFS Permissions
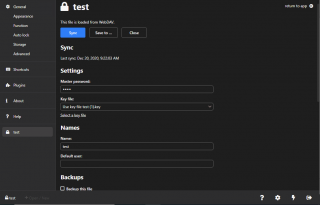
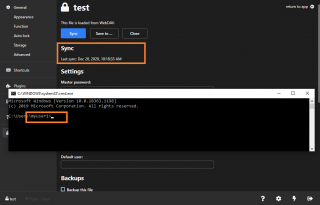
After configuring the authentication methods in IIS, we went back to the Keeweb software and tried to sync and save the changes in the kdbx database. As you can see on the screenshot below, the synching/saving process worked after enabling this setting.
Click on Picture for better Resolution
We thought that our configuration was completed…..However, we encountered another issue. We were performing our test using an account with administrative privileges on the IIS Web Server. As soon as a standard user account was used, the synching/saving process was not working anymore…..
Click on Picture for better Resolution
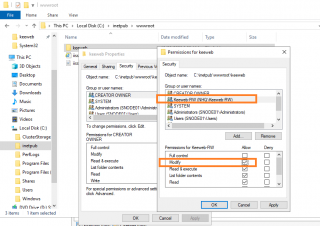
Looking at error code (HTTP 403), it was obvious that a standard user would not have the necessary rights to modify and change the kdbx file on the web share. To overcome this limitation, we have created an Active Directory Group (i.e. keeweb-RW). We have added the authorized users that could read and write into the keepass database. Then, we went to the location of the keeweb directory location and we have updated the NTFS permissions by granting Modify rights to the newly created group
Click on Picture for better Resolution
After logout/login operation, a user that was member of this new group was able to access the Keeweb interface and perform a sync/save operation succesfully….
Click on Picture for better Resolution
Final Notes
Voila ! This is it for this post.
We have seen that with some efforts, it possible to host the Keeweb application on premises using an IIS Web Server. Because the application is relying a lot on local storage, we have found out that the information and synching process during our investigation and testing process was not always accurate. We had to clear up the browser in order to have the expected behavior happening.
All in all, Keeweb on IIS can be a good alternative to cloud based or paid password management solution even if there are some configuration efforts that needs to be performed. We have demonstrated a really basic setup. Because Password management software is quite sensitive, additional security settings could be configured (IP address white list/black List, more granualar NTFS permissions, granular permissions at the WebDav level….)
We had fun playing around with Keeweb software and more specifically IIS web server.. Not a lot of posts were tackling Microsoft infrastructure and most of the posts we have seen were around Apache web server….We might come up with some additional posts about Keeweb on Apache Web server and/or nginx in the future
Till next time
See ya

Thank you for taking the time to research and post this. Normally, I would just make a shared drive on a segregated vlan and do a very lightweight password manager. But iis makes a lot of sense for keepass. We will give this a try.
@Shannon,
Thank you for visiting our blog and providing some feedback. For small environment this is working quite ok (even do the setup is not that straight forward). Hope this post can help…
Till next time
See ya