Hello World,
This post should be quite short but it’s important that you read it. Indeed, a security vulnerability was discovered affecting specific version of xRDP package software and the latest release of the package (i.e. 0.9.19) is providing the necessary fix for it. The vulnerability was classified as critical
So, today, we will try to provide necessary information that you need to be aware to patch and protect your system in case you are using the xRDP software solution…Let’s go…
Overview
Recent Releases
xRDP is basically the “Linux” version or implementation of Remote Desktop capabilities using RDP protocol. The team behind xRDP software tends to release a new version everyt 3 to 4 months and make the release cycle predictable. Recently, we published a quick post about the recent release of version 0.9.18 of xRDP software solution
A few weeks later, a new version was released (0.9.18.1) in February 2022 which was fixing an important security vulnerability that have been discovered. In march 2022, a newer version has been released as well. So, today, the most recent version of the xRDP package solution is 0.9.19
Discovered Vulnerability
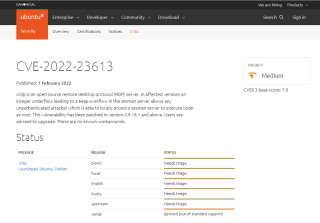
We have discovered the information about this vulnerability by “chance”. Indeed, since Ubuntu 22.04 is about to be released, we are preparing the next version of the xrdp-installer script. While testing the latest version, we noticed that the xrdp package version was indeed set to 0.9.19 (and not 0.9.18 anymore). After a quick search, we found out the issue about the security vulnerability. You can find more details about the issue at https://www.cve.org/CVERecord?id=CVE-2022-23613
In a nutshell, xRDP is affected by a privilege escalation issue. This situation can allow any unauthenticated attacker which can access locally the sesman server to execute code as root. There are no workarounds available and the only recommended way to fix this issue is to upgrade to version 0.9.18.1 or later.
This vulnerability is affecting the following version of xRDP
- 0.9.17
- 0.9.18
Since Linux Distributions might not ship with the latest version of xRDP package, you need to check if you are vulnerable or not…. For example, Ubuntu 22.04 (development branch) is shipping with xrdp package version 0.9.17 and based on the Ubuntu CVE web page, there is no patch available yet (https://ubuntu.com/security/cve-2022-23613).
Check your xRDP package version !!!
If you have performed a standard installation of xRDP (meaning using the package provided by the distribution maintainer), there is a good chance that you have older xRDP package version which should not be affected by the vulnerability. Ubuntu 21.10 and previous version were shipping with version 0.9.15 or lower.
However, if you have used our xrdp-installer script and you have use the custom installation mode, since we are getting the source files (of the latest release available at installation time), you will probably be running a more recent version which could be 0.9.17 or 0.9.18. These versions are affected by the vulnerability.
If you are in this situation, the best option would be to uninstall the xrdp version package you have and re-install it. If you have used the xrdp-installer script, you have to perform these operations via the script and the switch made available to you.
To check which version you are running, issue the following command on your system
xrdp -v
If you have version 0.9.17 or 0.9.18, (and you have used our xrdp-installer script), you can do the following
To remove the xrdp package, use the following switch
xrdp -r
We highly recommend you to reboot your system to ensure that you start again with a clean situation
To re-install the xrdp package (using our xrdp-installer script) that is not vulnerable to the vulnerability, you can issue one of the following commands
To install the xrdp package version from the distribution maintainer (from repository) xrdp-installer-1.3.sh To install the latest version of the xrdp package (version 0.9.19) that fix the security vulnerability xrdp-installer-1.3.sh -c
You can find all necessary information about the xrdp-installer script and how to use it in this post and link provided below
xRDP – Easy install xRDP on Ubuntu 18.04,20.04,21.04,21.10 (Script Version 1.3)
Note :
At time of writing, xrdp-installer is set to version 1.3 but a new version will be made available soon (end of April 2022). So please always ensure that you use the latest version of the script which can be found at https://www.c-nergy.be/products.html
Final Notes
This is it for this post !
This post is rather short but the information provided is quite important. xRDP version 0.9.17 and 0.9.18 are vulnerable. You need to check your system to see if you are affected or not by the vulnerability. Any previous version of xRDP (<0.9.17) is not affected. Any version running 0.9.18.1 or higher is not affected either.
Since we are working on the next version of the xrdp-script, we have noticed that Ubuntu 22.04 is shipping the version 0.9.17 and it seems there is no fix/patch made available yet. So, if you are planning to use Ubuntu 22.04, double-check the version of your xRDP software.
Finally, be aware, that we are planning to release soon (end of April), the next version of our xrdp-installer script. The next release will be a maintenance release to include support for Ubuntu 22.04. Another version might be made available later on introducing some more features…
Till next time
See ya

Hi,
I’ve written a long comment to explain my issue and the solution. My message has been rejected by wordpress as spam.
I don’t have time to write it again.
Long story short, to compile from source I have to modify the clone command @line 317 and add –recursive.
Otherwise libpainter cannot compile.
Regards,
Fred
@Fred,
Thank you for visiting our blog and providing feedback.. sorry about the spam “feature”… we will try to change and relax a little bit the configuration…. Thank you for sharing the info about git and recursive option. We have not yet encountered this issue but we know that some people came back with exactly the same issue and solution… We will test and check again this in the next script release and try to fix it
Again, thank you for letting us know 🙂
Till next time
See ya