Hello World,
Back again on the RDS 2012 R2 topic. With all the info, I’m publishing lately about this topic you should be fed up or you should be really happy to have us sharing all the small hick up we have encountered during our different projects.
The post of today should be quite short. We will explain a small issue we had while the RDS infrastructure was using a DMZ zone…
Let’s go
The RDS Setup
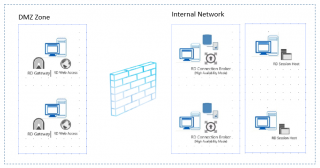
Based on the customer request, we have been asked to place the RD Gateway and the RD Web Access servers on a DMZ zone. These servers were accessible from the outside world. However, the RD Connection brokers and RD Session host servers were located on the internal network. You can see a high level view of the setup in the following drawing.
Click on Picture for Better Resolution
So, no problem we start performing the installation and working together with the Firewall team, we have opened the necessary ports needed to have such setup working.
Testing the Setup and the Failed connections
After having implemented all the rds infrastructure, it’s was time to perform some initial tests (load balancing, redundancy, access,…). At this stage, we encountered a small issue. While trying to access to the applications on the rd session hosts, an error was thrown or we never were able to perform the connection. the connection was simply dropping.
Using appropriate tools , we were able to assess that an access the RD Gateway servers. So, we were sure that the firewall was allowing traffic from the client to the RD Gateway. So the next logical step was to look into the RD Gateway and see if something was blocking the access to the RD Session Hosts.
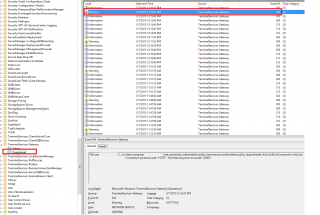
Looking into the event viewer, at the Applications and Services Logs > Microsoft > Windows >TerminalServices-Gateway node, we were able to retrieve the connections steps we were performing. Everything was fine till the warning message was thrown by the connection process.
Click on Picture for Better Resolution
Log Name: Microsoft-Windows-TerminalServices-Gateway/Operational
Source: Microsoft-Windows-TerminalServices-Gateway
Date: 10/7/2014 10:56:02 AM
Event ID: 304
Task Category: (3)
Level: Warning
Keywords: (16777216)
User: NETWORK SERVICE
Computer: XXXXXXXXXXX.wbc.local
Description:
The user “XXXXXX”, on client computer “XXX.XXX.XXX.XXX”, met connection authorization policy and resource authorization policy requirements, but could not connect to resource “ZZZZZZZZZZ”. The following error occurred: “23005”.
A lot of people on internet were pointing to the following link (https://technet.microsoft.com/en-us/library/ee891047(v=ws.10).aspx). The proposed resolution was to enable the remote desktop settings on the target servers. In our case, the remote desktop settings was enabled on the server. This was not our issues.
We had to search for another solution.
The Solution
It turns out that the problem was the connection between the RDWeb and the RD Connection Broker. The firewall port 3389 needs to be opened between the RDweb and the RD Connection broker. The firewall team didn’t know that the port 3389 needs to be open.
After the firewall team had open the port, we still had the issue. We had to open the firewall also on the RD Connection Broker Servers on the server itself (Windows Firewall). After authorizing the RDP traffic, we were able to perform our connection through the Remoteapp infrastructure.
Final Notes
Voila, this is it for this post. When you place RDS servers on the DMZ zone, ensure that your firewall infrastructure is configured accordingly.
Till next time
See ya
Hi team,
Im having the issue described and i would like to apply the fix, what i would like to know is in Windows Firewall what rules are you enabling or adding on the Connection Broker itself ?
Could you please provide more information on this step.
Thank you
Hi team,
Im having the issues described and i would like to apply the fix, what i would like to know is in Windows Firewall what rules are you enabling or adding on the connection broker itself?
Could you please provide more information on this step