|
|
The procedure does not works Ubuntu 23.10 and later. A new procedure needs to be used with these versions. Please Check this link
|
Hello World,
This post should have been published long time ago but we never had the opportunity. So, time to tackle this and publish the requested post….
Some users have been asked why it’s not possible to add users within remote session using the GUI interface. The reason behind this behavior is well known now and it’s called Polkit. Polkit is an application authorization framework that capture actions performed by a user and check if the use has been authorized to perform such action or not. Polkit reads some policy files that will specify if the user requested by the user is authorized, not authorized or need authentication.
Polkit provides a way to implement granular authorization to users based on the action requested but authorized actions can be different if you are locally logged on compared to user logged on remotely. By default, Polkit will block the possibility to add users to your Ubuntu system via the GUI Interface.
However, Polkit is flexible enough in order to create some custom rules and control what can be performed locally or remotely. In this post, we will see how we can allow user creation via GUI interface while remotely connected to your Ubuntu machine.
We already spoken extensively about Polkit technology and how to create exceptions. You can find more information about polkit, pkla and xrdp by reading these previous posts
Let’s do this…..
Overview
Disclaimer
Problem description
In our scenario, we are using an computer running Ubuntu 21.10. We have installed the xRDP software package using our famous xrdp-installer script (see xRDP – Easy install xRDP on Ubuntu 18.04,20.04,21.04,21.10 (Script Version 1.3)). Using xRDP software, we are able to perform a remote connection to our Ubuntu 20.04. So far, everything works as expected.
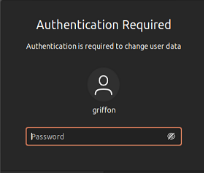
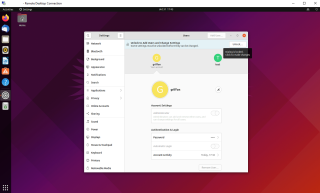
It’s time for us to add a user on the system. To perform this action, we open the System settings and locate users section. As shown in the screenshot, you would need administrative rights to be able to add users into the system. So far, the behavior between local and remote session are identical
Click on picture for better resolution
In the remote session, if you click on the unlock button, nothing will happens. No authentication prompt will be displayed. Nothing will show up. The only hint that can help you understand that polkit is blocking the functionality is when you hover on the “unlock” button and you can see the information “System Policy Prevent Changes”
Click on picture for better resolution
To enable this function, we need to tell Polkit that this action can be performed while remotely logged on…. keep reading 🙂
Solution : Create your custom rules
Create your custom pkla file
To allow addition of users on your system via remote session, we will need to create a text file under /etc/polkit-1/localauthority/50-local.d/. You need administrative privileges in order to write in this location !
Click on picture for better resolution
The file will be called 47-user-admin.pkla and should contains the following information
[user admin] Identity=unix-user:* Action=org.gnome.controlcenter.user-accounts.administration ResultAny=auth_admin_keep ResultInactive=no ResultActive=no
Save the file. You are ready to try your configuration…..
Testing your new rule
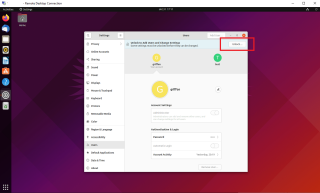
Again, you have to perform a remote connection to your Ubuntu machine. You will open again the System Settings, find the Users section. Since the custom pkla rule has been implemented, if you hover on the Unlock button, you will notice that the message has changed. It shows now “Dialog is locked. Click to make changes”
Click on picture for better resolution
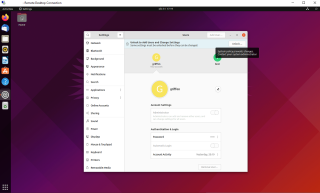
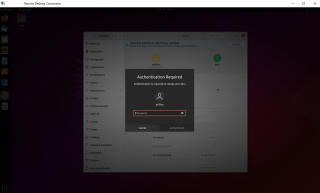
If you click on the Unlock button, you will see that an authentication dialog box is displayed.
Click on picture for better resolution
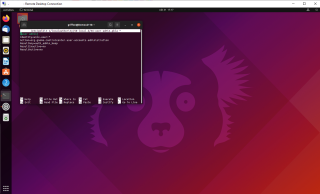
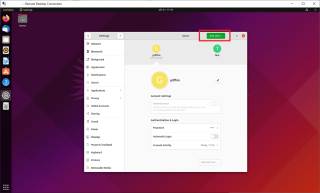
Provide the password for an admin account and you will see that you should be able to add new users from the GUI. The Add user button is available and you can proceed with your user creation process
Click on picture for better resolution
Another option : the command line
As a side note, note that’s always possible to create user account remotely or locally using the command line tool “adduser”. If you use the command line approach, there is no need to create a custom rule file and no need to modify the polkit configuration….
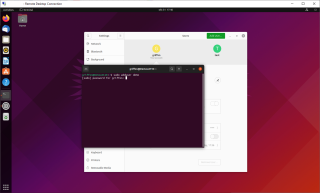
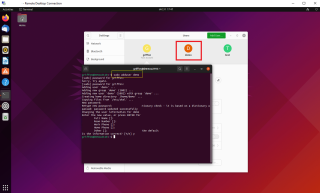
To create user via command line, you simply need to issue the following command in a Terminal session
sudo adduser <%UserName%>
Click on picture for better resolution
You will be prompted for a password. Provide the password and answer the question asked by the utility and you will see that your account will be created accordingly
Click on picture for better resolution
Final Notes
This is it for this post !
As you can see, it’s relatively easy to configure your system to allow users to create user account through the Graphical Interface when remotely connected using xRDP software. At first, this can look strange that a user has not the same authorization rules while logged on locally or logged remotely. But when you understand what’s causing the behavior (i.e. Polkit technology), you can configure your system accordingly and create some exceptions to allow actions when remotely connected.
We have finally published this long awaited post….Time to move the next one… Possibly we could add this code into our famous xrdp-installer script….
Till next time
See ya
Great. But what I really need, is a way to have polkit accept xrdp sessions as local, without having to code a zillion exceptions.
Why? Because I use an iPad Pro with MagicKeyboard connected with a USB-C cable to a RasPi in connection with xRDP essentially as console. All xRDP connections to that RasPi are “local” in the sense that the iPad Pro replaces a power supply, screen, mouse, and keyboard for the RasPi. Only on the rarest of cases (forced upon me by Polkit) do I hook up the RasPi to some screen to change some things.
So, yes, access to local audio, bluetooth, etc. etc.
The audio part I could fix by modifying the xrdp pluseaudio configuration.
But lots of small things remain, and it’s always the same: it’s not considered a local session.
@rcfa,
Thank you for visiting our blog and sharing your experience. Technically you could totally disable polkit feature if you want to or you could create a pkla file exception where you would specify that all actions are allowed something like (this is an example, you might have to tweak it to your needs)
[xRDP All Actions Allowed]Identity=unix-group:users
Action=*
ResultAny=yes
ResultInactive=yes
ResultActive=yes
Hope this help
Till next time
See ya
This is great. We were struggling with this.
Thank you!
@Griffon ubuntu does not seem to just ignore unix-group when used in polkit rules now. Is this a new development?
@Vegard,
thank you for visiting our blog and sharing your findings… Since you do not provide any information about the Ubuntu version you are using, we would guess that you are running Ubuntu 23.10. The polkit version seems to have been upgraded to a more recent version and indeed, the behavior will be different.. If the version is different, the pkla file is not valid anymore and you should use a javascript script based file structure
We will try to update this post…. to take into account the new version of polkit
Hope this help
Till next time
See ya
Ubuntu 23.10 solution? İm waiting sir.
@Nazim,
Thank you for visiting our blog and providing some feedback. So, please be aware that the information to enable this on Ubuntu 23.10 and later has been already published on our blog on November 2023.
You can find the necessary steps in the following post (xRDP – Can’t unlock users settings in Ubuntu 23.10
We have added an additional link in the original post that will redirect users to this new procedure
Hope this help
Till next time
See ya