Hello World,
In one of our previous post , we have described how to prevent login into the Remote Host session servers. When you prevent interactive login, you are effectively blocking access to your RDS infrastructure. A user that tries to start a remoteapp application from the RD web Access server or if he tries to directly connect to the RDS server, an error will occur and the service will not be accessible.
So, in some circumstances, you want to have your users consume services from the RDWeb Access server but prevent them to login into the Remote desktop server. So, the options explained in the previous post are not valid for this specific case scenario.
Blocking Full Desktop Access Process
To find a way to block full desktop access while having the remoteapp infrastructure working was kind of challenging. We have tried multiple things and the only one that was really working and quite simple to implement was to use again some Active Directory attributes and populate them accordingly. Googling around, it also seems that the most used approach to block full desktop access.
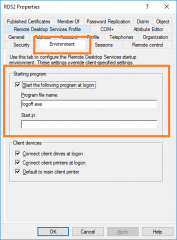
Basically, you will locate your user account in Active directory. Right-click on it > Select Properties. In the properties dialog box, you go to environment tab. In the Start following program at startup, you can specify a program that would launch when the user logins and perform some actions that would logout the user as soon as it tries to perform the action.
Click on Picture for Better Resolution
The most used program is the logoff.exe. This builtin exe perform exactly the required action you are looking for. Logging off the user if he tries to connect directly to the RDS Host session server. This approach meets your requirements but does not provide any information to the user. It might be better to develop a custom program that could provide some feedback to your user….
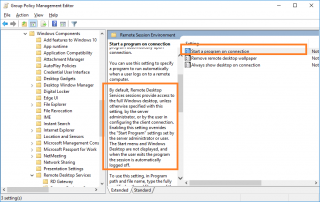
You can apply this on a per user base or you can use a GPO that will implement this setting to your user community in more controlled way and efficient way. You can implement indeed a GPO that will control the Remote Session variables (this is a user policy) and you should achieve the same results
Click on Picture for Better Resolution
Final Notes
This approach will ensure that users can use the remoteapp published applications (via the RD Web Access server) but users would not be able to perform a direct connection to the RD Host session servers being part of the RDS Farm. This is a simple way to prevent user to have indeed access to all local resources. Actually, you would need to perform some additional configuration and hardening activities in order to ensure that a normal user cannot damage your system.
If a user has access to cmd.exe, powershell.exe or Explorer.exe via the remoteapp, the user will be able to access local resources or executable and still make some damages. This is where you will need to implement additional gpos that would then block access to mmc console or applications using Applocker settings
Hope you enjoyed this post
Till next time
See ya